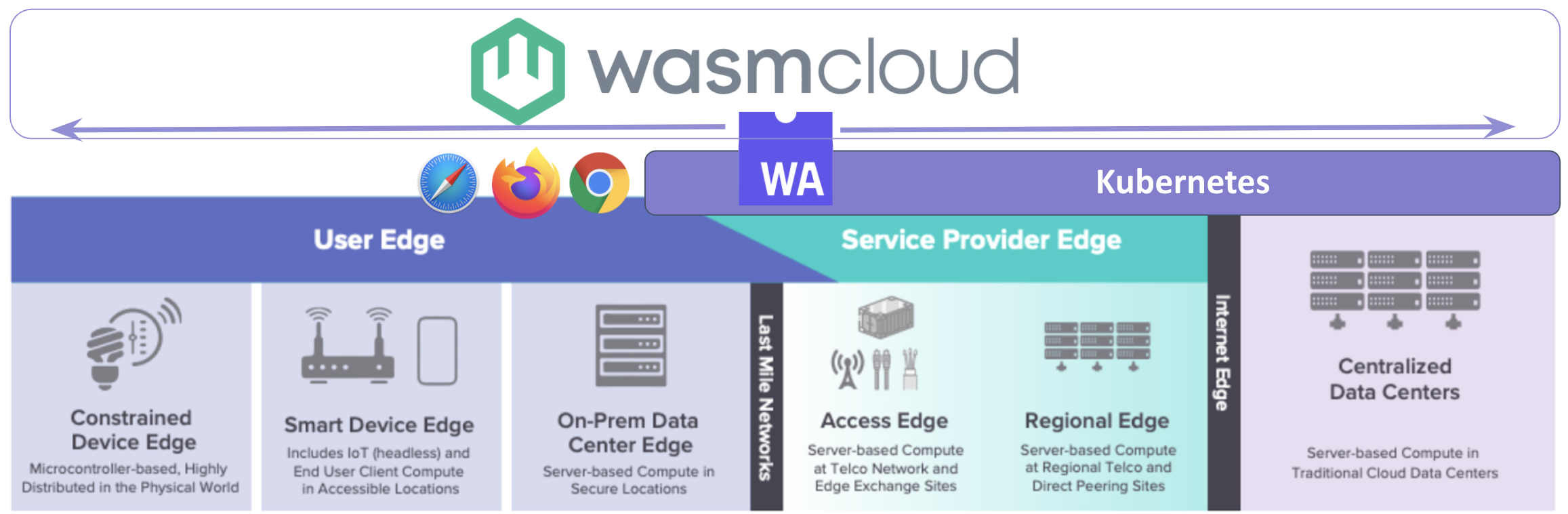
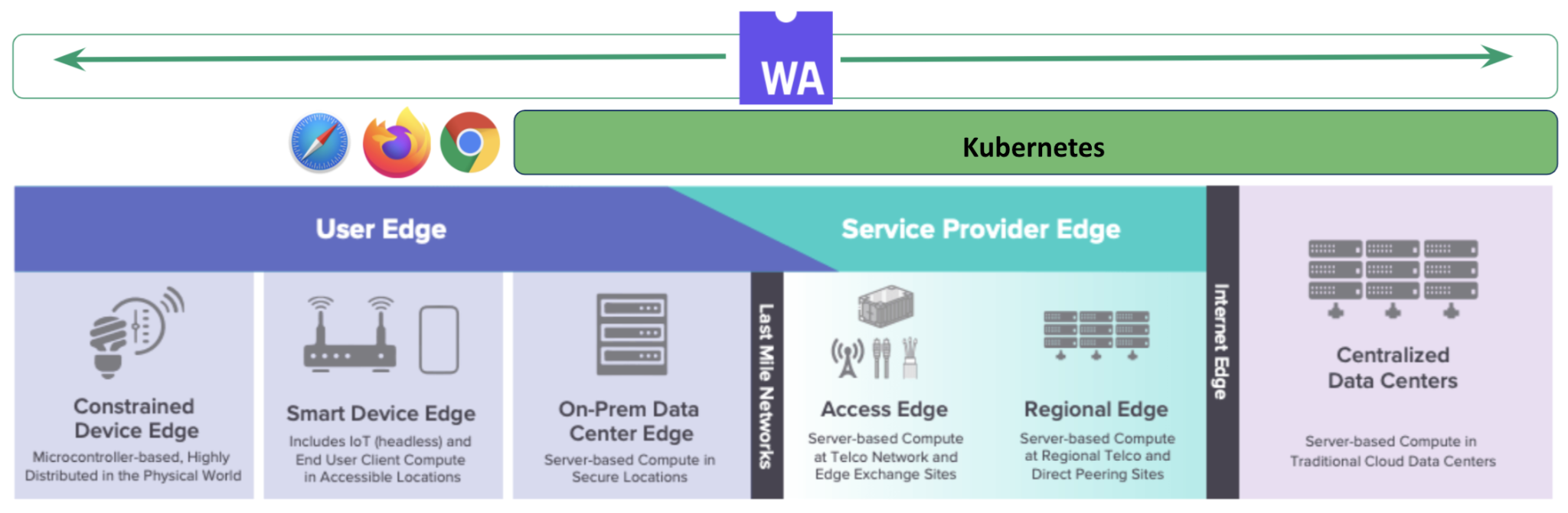
There is nothing more chaotic today than the current state of cybersecurity.
In my latest article in The New Stack, “How Web Assembly Can Mitigate the Software Supply Chain Crisis,” I discussed the relative ease with which today’s predominant method for building software allows for malware infection across all components of an application.
Until now, the method for building software relied on the aggregation of software components that often lack distinct security boundaries between them.